The Layered Journey of Network Communication
When two devices talk, they send little data packages called PDUs
First Listen: let your ears lead the way before your mind takes notes.
📻 FZ2CCNA Radio:
Then read: let your eyes explore before your mind starts to explain.
A New Way to Understand Network Communication
Imagine a wind-swept shoreline stretching to the ends of the earth. In your hand, you hold a message — a personal one. Maybe it’s a whisper to a friend, a file to a colleague, or a command to a faraway server. Whatever it is, it must travel across vast, invisible networks.
But this isn’t a fantasy. There’s no magical seagull, enchanted bottle, or quantum teleportation. There is, instead, something even more impressive: a protocol-driven journey powered by layers of invisible agents. Each layer with a single, disciplined task — preparing, guiding, and delivering that message with absolute precision.
This is data encapsulation — not a buzzword, but the quiet hero of modern communication. And today, we’re going to follow that message, step by step, layer by layer, all the way from your fingertips to its final destination.
You Write, They Deliver
To the human eye, sending a message online feels like a single action. One click, one push, and it’s gone. But behind that instant lies a hidden process as orderly as a military operation and as elegant as a symphony.
When you send data, it’s not pushed off a cliff. It’s handed off — carefully, layer by layer — with each step adding context, instructions, and protection. Like a message passed between trusted hands in a relay, every layer wraps the message in new information before passing it down.
That’s encapsulation. A transformation process where your raw message is turned into a traveler — a PDU — armed with everything it needs to survive the journey.
Let’s follow that transformation.
The Briefing Room (Application Layer)
Everything begins at the top: the Application Layer — the bridge between your human intention and the technical machinery of the network.
When you click “Send,” upload a photo, or access a website, you’re not thinking about packets or ports. You’re simply expressing a desire. The application you’re using — whether it’s a browser, an email client, or a messaging app — takes that desire and turns it into data.
At this point, the data is fragile. It’s pure meaning without context. It has no label, no ID, no instructions. It’s like a handwritten note with no envelope, no address, and no sense of the outside world.
But this is the job of the Application Layer: to format and prepare that raw message, giving it structure and purpose so the layers below can begin their work.
The message is ready. But the journey hasn’t even started yet.
The Tactical Wrap (Transport Layer)
Enter the Transport Layer — the meticulous organizer, the protocol general.
Here, the message gains its first serious armor. The Transport Layer takes that application data and encapsulates it into a structure called a segment. But that’s not all — it also assigns the message a unique port number, which tells the receiving device where this message should be delivered.
Imagine a giant building full of offices. The IP address might get the letter to the building, but the port number ensures it lands on the right desk. Without ports, everything would end up dumped at the front lobby.
Beyond routing, this layer also decides whether to send the message with reliability guarantees (TCP) — checking that it arrives, in order, and intact — or to send it out quickly and without ceremony (UDP), useful for live video, voice, or real-time games.
Now your message is more than just content — it’s a complete unit of communication. It can be tracked, verified, and is ready to travel deeper through the network stack.
The Navigator (Network Layer)
With a segment ready for travel, the Network Layer now steps in to figure out the where.
Think of this layer as the GPS for your message. It determines the path across networks — whether it’s from your home router to a server in California, or from your phone to a data center in Singapore.
The Network Layer adds an IP header — a label that includes the source and destination IP addresses. This makes the segment identifiable to routers all over the world. These devices don’t care what’s inside. Their only job is to look at the IP address and forward the message closer to its goal.
Once this layer finishes its job, the segment is now officially a packet. It knows where it came from. It knows where it’s going. And it’s ready to take on the outside world.
But it’s still not ready to physically move.
The Street Crew (Data Link Layer)
Now the packet needs to get from one physical device to the next — maybe from your PC to the router, or from the router to a switch. This is where the Data Link Layer shines.
Here, the packet is placed into a frame, which includes two key additions:
- A MAC address header, pointing to the next-hop device.
- A trailer that includes error-checking information (usually a CRC).
This layer doesn’t look at the IP address. It doesn’t care about port numbers. It’s concerned only with local delivery — moving the frame to the next device along the chain.
You can think of it as a taxi cab taking the packet to the next bus stop. It won’t take it across the country, but it will get it to the place where bigger decisions are made.
Now, with all layers in place, your message is fully dressed for travel.
The Leap of Faith (Physical Layer)
Here comes the jump.
The frame is now broken into bits — tiny electrical pulses, light flashes, or radio waves — depending on the transmission medium.
This is the Physical Layer: the final step between thought and movement.
Here, the data becomes real. It travels as patterns of voltage across copper wires, as photons down fiber-optic strands, or as modulated waves through the air.
From here, it vanishes from your device’s memory — but it’s now alive on the network, hurtling toward its destination.
And you? You probably never noticed it left.
Decapsulation
On the receiving end — in another machine, maybe miles away — the message arrives not as a full document, but as pulses, waves, and bits.
And now, the process reverses.
- Physical Layer: Reassembles bits into recognizable binary.
- Data Link Layer: Validates the frame’s integrity and checks its MAC address.
- Network Layer: Confirms the packet’s destination IP and forwards it upward.
- Transport Layer: Identifies the correct application based on port number.
- Application Layer: Delivers the original message to the software waiting for it.
What arrives is exactly what you sent. No more. No less.
Wrapped, guided, delivered — and finally unwrapped again.
Protocol Data Units: The Evolution of a Message
Each layer gives your message a new name, a new form — a new identity. These forms are called Protocol Data Units (PDUs):
- Segment at the Transport Layer (with port numbers)
- Packet at the Network Layer (with IP addresses)
- Frame at the Data Link Layer (with MAC addresses)
- Bits at the Physical Layer (raw transmission)
Each PDU wraps the one above it like layers of armor — always carrying the same sacred core: the payload.
Payload: The Heart That Never Changes
At the center of every encapsulated unit is the payload — the original data created by the application.
Every header or trailer added by the layers serves one purpose only: to protect, guide, or deliver this payload more efficiently.
The payload doesn’t change. It doesn’t care what network it travels through or how it’s wrapped. Its only concern is getting to the application that understands it.
That’s the true beauty of encapsulation: the data stays pure, even when the world around it is chaotic.
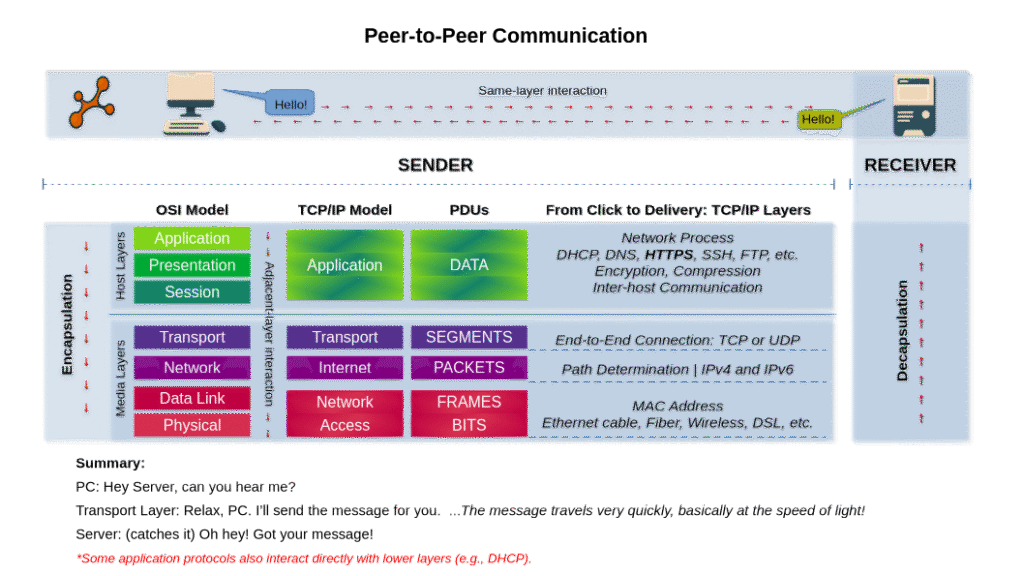
Who Talks to Whom? Layer Interactions Explained
Networking is a game of hierarchies and mirrors.
- Adjacent-layer interaction happens within the same device. Each layer serves the one above and depends on the one below. Like colleagues on a team, each does their part in sequence.
- Same-layer interaction happens between devices. The Transport Layer on one device is trying to coordinate with the Transport Layer on the other — even though it can’t speak to it directly. So, it embeds its message in a header, trusting the stack to deliver it across.
It’s like diplomats exchanging sealed letters, carried by staff, transported by guards, delivered across oceans — but only ever understood by their counterparts.
Each layer trusts the others to do their jobs. And that trust builds the internet.
Encapsulation: Discipline Behind the Curtain
Encapsulation is more than a process. It’s a contract. An architecture. A brilliant method to take messy human data and convert it into something machines can move with elegance and precision.
Without encapsulation, data would get lost. Misrouted. Broken.
With it, we achieve order out of chaos.
Messages flow. Videos stream. Lives connect.
You don’t see it happening — but it’s happening all the time, in the background, flawlessly.
CCNA Takeaways (Don’t Just Read — Own This)
- Encapsulation wraps data as it moves down the stack.
- De-encapsulation unwraps it as it moves up on the receiver.
- Know your PDU by layer:
- L4 → Segment → Ports and Protocols
- L3 → Packet → Routers (IPv4 and IPv6)
- L2 → Frame → Switches (MAC address)
- L1 → Bits → Cables or Radio waves (Electric, Laser, Light and Radio waves signals)
- The payload is the untouched core, carried and delivered.
- Adjacent-layer interaction = service within the same device.
- Same-layer interaction = communication between peers on different devices.
Final Thought: Every Message Is a Journey
Next time you send a message, don’t think of it as a file transfer. Think of it as an expedition — one that navigates ports, addresses, networks, devices, and physics.
You are the author of that message.
The layers are its guardians.
And the internet? Just the road.
What Did You Learn Today?
Let’s Find Out!
Instructions
- Select the correct answer for each technology concept.
- All questions pertain directly to the networking technologies explained.
- After answering, click “See Result” to see your score and feedback.
[Return to CCNA Study Hub] — Next Stop: [Section 2 | Cisco IOS Operations] …Currently Buffering… Available Soon!
